Secure Resource Verification
The following is a list of publications made in this project:
On the Security of Bottleneck Bandwidth Estimation Techniques: We investigate the vulnerabilities of current bottleneck bandwidth estimation techniques in adversarial settings. We show that finding “full fledged” solutions for the multitude of attacks on the end-to-end bandwidth estimation process might not be feasible in the absence of trusted network components;. We discuss possible solutions that alleviate these threats without requiring trusted infrastructure support.
Secure Remote Execution of Sequential Computations: We describe a scheme that secures the remote execution of sequential computations in grid-computing scenarios. To the best of our knowledge, this is the first contribution that addresses the security of generic sequential computations. We further investigate the damages introduced by possible chaining of errors within the remote execution and we discuss recovery mechanisms to counter these challenges.
Low-Cost Client Puzzles based on Modular Exponentiation: We propose a new, nonparallelizable verification-efficient client puzzle. Our puzzle is based on modular exponentiation and enables efficient verification of the puzzle solution that is reported by the client (prover). More specifically, we show that the the puzzle verification burden can be securely transferred to the prover that executes the puzzle.
Privacy-Preserving Outsourcing of Brute-Force Key Searches: We consider a problem where a supervisor holds a ciphertext and wants to search for the corresponding key assisted by a set of helper nodes, without the nodes learning any information about the plaintext or the decryption key. We call this a privacy-preserving cryptographic key search. We introduce two types of privacy-preserving key search problems: plaintext-hiding and key-hiding cryptographic search. We discuss possible constructions of privacy-preserving solvers for plaintext-hiding and key-hiding searches in private-key cryptography.
Pay as you Browse: Microcomputations as Micropayments in Web-based Services: We propose a micropayment model for non-specialized commodity web-services based on microcomputations. In our model, a user that wishes to access online content offered by a website does not need to register or pay to access the website; instead, he will accept to run microcomputations on behalf of the website in exchange for access to the content. We analyze the security and privacy of our proposal and we show that it ensures payment for the content while preserving the privacy of users.
Syssec members on the project:
- Ghassan Karame, Srdjan Capkun.
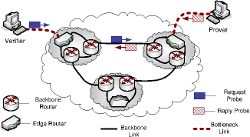
On the Security of Bottleneck Bandwith Estimation Techniques
Several wide-area services are increasingly relying on bottleneck bandwidth estimation tools to enhance their network performance. Selfish hosts have, therefore, considerable incentives to fake their bandwidths in order to increase their benefit in the network. In this work, we address this problem and we investigate the vulnerabilities of current bottleneck bandwidth estimation techniques in adversarial settings. We show that finding “full-fledged” solutions for the multitude of attacks on the end-to-end bandwidth estimation process might not be feasible in the absence of trusted network components; we discuss solutions that make use of such trusted components. Nevertheless, we discuss other possible solutions that alleviate these threats without requiring trusted infrastructure support and we evaluate the effectiveness of our proposals on PlanetLab nodes.
Related Publications:
- Ghassan Karame and Srdjan Capkun, On the Security of End-to-End Network Measurements ETH Zurich, D-INFK, Technical Report No. 628, June 2009. [DownloadPDF (PDF, 287 KB)vertical_align_bottom | Downloadbibtex (BIB, 298 Bytes)vertical_align_bottom].
- Ghassan Karame, David Gubler and Srdjan Capkun, On the Security of Bottleneck Bandwidth Estimation Techniques, In Proceedings of SecureComm (International Conference on Security and Privacy in Communication Networks), 2009. [DownloadPDF (PDF, 916 KB)vertical_align_bottom | Downloadbibtex (BIB, 384 Bytes)vertical_align_bottom].
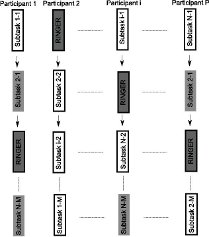
Secure Remote Execution of Sequential Computations
We describe a scheme that secures the remote execution of sequential computations in grid-computing scenarios. To the best of our knowledge, this is the first contribution that addresses the security of generic sequential computations. By dividing sequential tasks into smaller subtasks and permuting them among participants, we show that our scheme facilitates the insertion of selective redundancy and/or pre-computed functions (ringers) that are indistinguishable from other computations.We analyze the security of this proposal and we demonstrate that our scheme enables the detection of individual and colluding malicious participants. In addition, we show that our scheme can be equally used to securely track the progress of remote execution. We further investigate the damages introduced by possible chaining of errors within the remote execution and we discuss recovery mechanisms to counter these challenges. We validate our findings both analytically and empirically via simulations.
Related Publications:
- Ghassan Karame, Mario Strasser, Srdjan Capkun, Secure Remote Execution of Sequential Computations, In Proceedings of ICICS (International Conference on Information and Communications Security), 2009 . [DownloadPDF (PDF, 238 KB)vertical_align_bottom | Downloadbibtex (BIB, 363 Bytes)vertical_align_bottom].
Low-Cost Client Puzzles Based on Modular Exponentiation
Client puzzles have been proposed as a useful mechanism for mitigating Denial Of Service attacks on network protocols. While several puzzles have been proposed in recent years, most existing non-parallelizable puzzles are based on modular exponentiations. The main drawback of these puzzles is in the high cost that they incur on the puzzle generator (the verifier). In this paper, we propose cryptographic puzzles based on modular exponentiation that reduce this overhead. Our constructions are based on a reasonable intractability assumption in RSA: essentially the difficulty of computing a small private exponent when the public key is larger by several orders of magnitude than the semi-prime modulus. We also discuss puzzle constructions based on CRT-RSA. Given a semi-prime modulus N , the costs incurred on the verifier in our puzzle are decreased by a factor of |N |/k when compared to existing modular exponentiation puzzles, where k is a security parameter. We further show how our puzzle can be integrated in a number of protocols, including those used for the remote verification of computing performance of devices and for the protection against Denial of Service attacks. We validate the performance of our puzzle on a large number of PlanetLab nodes.
Related Publications:
- Ghassan Karame, Srdjan Capkun, Low-Cost Client Puzzles based on Modular Exponentiation, in Proceedings of ESORICS (European Symposium on Research in Computer Security), 2010 [DownloadPDF (PDF, 261 KB)vertical_align_bottom | Downloadbibtex (BIB, 270 Bytes)vertical_align_bottom].
Privacy-Preserving Outsourcing of Brute-Force Key Searches
In this work, we investigate the privacy-preserving properties of encryption algorithms in the special case where encrypted data might be brute-force decrypted in a distributed setting. For that purpose, we consider a problem where a supervisor holds a ciphertext and wants tosearch for the corresponding key assisted by a set of helper nodes, without the nodes learning any information about the plaintext or the decryption key. We call this a privacy-preserving cryptographic key search. We provide a model for privacy-preserving cryptographic searches and we introduce two types of privacy-preserving key search problems: plaintext-hiding and key-hiding cryptographic search. We show that a number of private-key and public-key encryption schemes enable the construction of efficient privacy-preserving solvers for plaintext hiding searches. We also discuss possible constructions of privacy-preserving solvers for key-hiding cryptographic searches.
Our results highlight the need to consider the property of enabling efficient privacy-preserving solvers as an additional criterion for choosing which cryptographic algorithm to use.
Related Publications:
Ghassan Karame, Srdjan Capkun and Ueli Maurer, Privacy-Preserving Outsourcing of Brute-Force Key Searches, ETH Zurich, D-INFK, Technical Report No. 662, 2010.
Ghassan Karame, Srdjan Capkun, Ueli Maurer, Privacy-Preserving Outsourcing of Brute-Force Key Searches, In Proceedings of the ACM Cloud Computing Security Workshop (CCSW); in conjunction with ACM CCS, 2011.
Pay as you Browse: Microcomputions as Micropayments in Web-Based Services
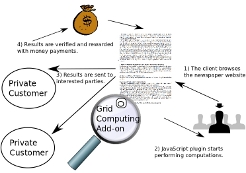
Currently, several online businesses deem that advertising revenues are not enough on their own to generate profits and are set to charge for online content. In this work, we explore a complement to the current advertisement model; more specifically, we propose a micropayment model for non-specialized commodity web-services based on micro-computations. In our model, a user that wishes to access online content offered by a website does not need to register or pay to access the website; instead, he will accept to run microcomputations on behalf of the website in exchange for access to the content. These microcomputations could support ongoing computing projects that have clear benefits (e.g., projects relating to HIV, dengue, cancer, etc.). We argue that this micropayment model is economically and technically viable and that it can be integrated in existing distributed computing frameworks (e.g., the BOINC platform). We implement a preliminary prototype through which we evaluate the performance and usability of our proposed model. Finally, we analyze the security and privacy of our proposal and we show that it ensures payment for the content while preserving the privacy of users.
Related Publications:
Ghassan Karame, Aurelien Francillon, Srdjan Capkun, Pay as you Browse: Microcomputations as Micropayments in Web-based Services, In Proceedings of the International World Wide Web Conference (WWW), 2011 [DownloadPDF (PDF, 1.3 MB)vertical_align_bottom | Downloadbibtex (BIB, 297 Bytes)vertical_align_bottom].
