SPOT: Secure Positioning (Localization)
The goal of the Secure POsiTioning (SPOT) project is to investigate techniques for the secure location determination of wireless device. This is also known as secure localization. In the past, the problem of positioning in wireless networks has mainly been studied in a nonadversarial setting; this, however, is a non-realistic assumption in many newly emerging scenarios (e.g., alarm systems, verticular ad-hoc networks). To mitigate possible attacks, several mechanisms have been proposed in the framework of SPOT. These include mechanisms for secure position (location), distance and encounter verification of wireless devices. They enable to securely determine the position of a device, estimate its distance, and track its motion.
Existing (secure or insecure) positioning techniques in wireless networks are generally based on the presence of infrastructure nodes and further rely on the time, time difference, strength or angle of arrival of transmitted signals. Different signal propagation times for, e.g., radio or ultrasonic signals, may be used in the positioning. On a global scale, navigation signals from satellites are used.
We proposed or contributed to the following proposals for secure localization and location verification in wireless networks; further information and related publications are given below:
Physical-layer Attacks on Chirp-based Systems: Investigation of physical-layer distance modification attacks on chirp-based ranging systems.
Design and Implementation of a Terrorist-Fraud Resilient Distance Bounding System: A new, hybrid digital-analog design that enables the implementation of Terrorist Fraud resilient distance bounding protocols.
On the Requirements for Successful GPS Spoofing Attacks: Investigation of the requirements for successful GPS spoofing attacks on individuals and groups of victims with civilian or military GPS receivers.
GDB: Group Distance Bounding Protocols: Distance bounding protocols in group settings
Distance Hijacking Attacks on Distance Bounding Protocols: A new type of attack on Distance Bounding protocols - Distance Hijacking
Relay Attacks on Passive Keyless Entry and Start Systems in Modern Cars: We demonstrate relay attacks on Passive Keyless Entry and Start (PKES) systems used in modern cars. We build two efficient and inexpensive attack realizations, wired and wireless physical-layer relays, that allow the attacker to enter and start a car by relaying messages between the car and the smart key.
Secure Ranging With Message Temporal Integrity: Enabling the detection of delay attacks on ranging systems
Realization of RF Distance Bounding: We build a prototype system that demonstrates that radio distance bounding protocols can be implemented to match the strict processing times that distance bounding protocols require.
Location Privacy Of Distance Bounding Protocols: We show that distance bounding protocols leak information about the location and distance between communicating partners
Location spoofing on WLAN-based localization: Security analysis and demonstration of possible attacks on WLAN-based localization schemes
UWB-based secure ranging and localization: Secure localization system based on the first implementation of UWB secure ranging
Secure broadcast localization and time synchronization: Secure localization for navigation systems based on Integrity-coding
Secure localization using hidden and mobile stations: Location verification and secure localization based on hidden infrastructure nodes
Verifiable multilateration: Location verification and secure localization using distance-bounding and authenticated ranging
Secure RSS-based localization: Secure localization using ranging based on the received signal strength (RSS) and propagation delay measurements
Secure verification of node encounters (SECTOR): Proximity verification in mobile ad-hoc networks using distance-bounding
Syssec members on the project:
- Srdjan Capkun, Christina Pöpper, Nils Ole Tippenhauer, Aanjhan Ranganathan
Past members:
- Kasper Rasmussen
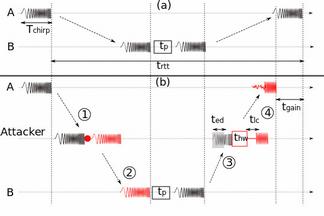
Physical-Layer Attacks on Chirp-Based Ranging Systems
Chirp signals have been extensively used in radar and sonar systems to determine distance, velocity and angular position of objects and in wireless communications as a spread spectrum technique to provide robustness and high processing again. Recently, several standards have adopted chirp spread spectrum (CSS) as an underlying physical-layer scheme for precise, low-power and low-complexity real-time localization. While CSS-based ranging and localization solutions have been implemented and deployed, their security has so far not been analyzed. In this work, we analyze CSS-based ranging and localization systems. We focus on distance decreasing relay attacks that have proven detrimental for the security of proximity-based access control systems (e.g., passive vehicle keyless entry and start systems). We describe a set of distance decreasing attacks realizations and verify their feasibility by simulations and experiments on a commercial ranging system. Our results demonstrate that an attacker is able to effectively reduce the distance measured by chirp-based ranging systems from 150 m to 700 m depending on chirp configuration. Finally, we discuss possible countermeasures against these attacks.
Related Work:
Aanjhan Ranganathan, Boris Danev, Aurélien Francillon, Srdjan Capkun
Physical-Layer Attacks on Chirp-based Ranging Systems
In Proceedings of ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2012
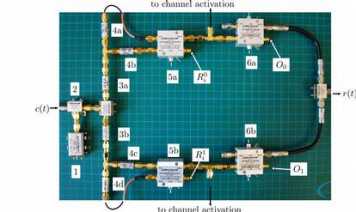
Design and Implementation of a Terrorist Fraud Resilent Distance Bounding System
Given the requirements of fast processing and the complexity of RF ranging systems, distance bounding protocols have been challenging to implement so far; only few designs have been proposed and implemented. Currently, the most efficient implementation of distance bounding protocols uses analog processing and enables the prover to receive a message, process it and transmit the reply within 1 ns, two orders of magnitude faster than the most efficient digital implementation. However, even if implementing distance bounding using analog processing clearly provides tighter security guarantees than digital implementations, existing analog implementations do not support resilience against Terrorist Fraud attacks; they protect only against Distance Fraud and Mafia Fraud attacks. We address this problem and propose a new, hybrid digital-analog design that enables the implementation of Terrorist Fraud resilient distance bounding protocols. We introduce a novel attack, which we refer to as the “double read-out” attack and show that our proposed system is also secure against this attack. Our system consists of a prototype prover that provides strong security guarantees: if a dishonest prover performs the Terrorist Fraud attack, it can cheat on its distance bound to the verifier only up to 4.5 m and if it performs Distance Fraud or Mafia Fraud attacks up to 0.41 m. Finally, we show that our system can be used to implement existing (Terrorist Fraud resilient) distance bounding protocols (e.g., the Swiss Knife and Hancke-Kuhn protocol) without requiring protocol modifications.
Related Work:
Aanjhan Ranganathan, Nils Ole Tippenhauer, Boris Skoric, Dave Singelee and Srdjan Capkun
Design and Implementation of a Terrorist-Fraud Resilient Distance Bounding System
In Proceedings of 17th European Symposium on Research in Computer Security (ESORICS), 2012
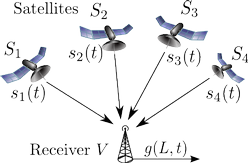
On the Requirements for Successful GPS Spoofing Attacks
An increasing number of wireless applications rely on GPS signals for localization, navigation, and time synchronization. However, civilian GPS signals are known to be susceptible to spoofing attacks which make GPS receivers in range believe that they reside at locations different than their real physical locations.
We investigate the requirements for successful GPS spoofing attacks on individuals and groups of victims with civilian or military GPS receivers. In particular, we are interested in identifying from which locations and with which precision the attacker needs to generate its signals in order to successfully spoof the receivers. We show, for example, that any number of receivers can easily be spoofed to one arbitrary location; however, the attacker is restricted to only few transmission locations when spoofing a group of receivers while preserving their constellation.
In addition, we investigate the practical aspects of a satellite-lock takeover, in which a victim receives spoofed signals after first being locked on to legitimate GPS signals. Using a civilian GPS signal generator, we perform a set of experiments and find the minimal precision of the attacker’s spoofing signals required for covert satellite-lock takeover.
Related publication:
- Nils Ole Tippenhauer, Christina Pöpper, Kasper Bonne Rasmussen, Srdjan Capkun
On the Requirements for Successful GPS Spoofing Attacks
In Proceedings of the ACM Conference on Computer and Communications Security (CCS), 2011 [Download PDF (PDF, 1.2 MB)]
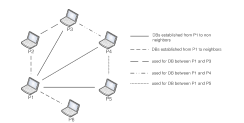
GDB: Group Distance Bounding Protocols
Secure distance bounding (DB) protocols allow one entity, the verifier, to securely obtain an upper-bound on the distance to another entity, the prover. Thus far, DB was considered mostly in the context of a single prover and a single verifier. There has been no substantial prior work on secure DB in group settings, where a set of provers interact with a set of verifiers. The need for group distance bounding (GDB) is motivated by many practical scenarios, including: group device pairing, location-based access control and secure distributed localization. GDB is also useful in mission- critical networks and automotive computer systems. This paper addresses, for the first time, GDB protocols by utilizing the new passive DB primitive and the novel mutual multi-party GDB protocol. We show how they can be used to construct secure and efficient GDB protocols for various settings. We analyze security and performance of our protocols and compare them with existing DB techniques when applied to group settings.
Related Work:
Srdjan Capkun, Karim El Defrawy, Gene Tsudik
Group Distance Bounding Protocols (short paper)
In Proceedings of the 4th International Conference on Trust and Trustworthy Computing (TRUST), 2011
Related technical report: [Download PDF (PDF, 1.1 MB)]
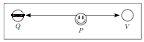
Distance Hijacking Attacks on Distance Bounding Protocols
Distance bounding protocols are typically analyzed with respect to three types of attacks: Distance Fraud, Mafia Fraud, and Ter rorist Fraud. We define a fourth main type of attacks on distance bounding protocols, called Distance Hijacking attacks. We show that many proposed distance bounding protocols are vulnerable to these attacks, and we propose solutions to make these protocols resilient to Distance Hijacking. Additionally, we generalize Distance Hijacking to Location Hijacking, to which location verification protocols may be vulnerable.
Distance Hijacking Attack
Related Work:
Cas Cremers, Kasper Bonne Rasmussen, Srdjan Capkun
Distance Hijacking Attacks on Distance Bounding Protocols
Cryptology ePrint Archive: Report 2011/129, 2011 [Download PDF (PDF, 638 KB)]

Relay Attacks on Passif Keyless Entry and Start Systems in Modern Cars
Modern cars embed complex electronic systems in order to improve driver safety and convenience. Traditionally, access and authorization have been achieved using physical key and lock systems, where by inserting a correct key into the door and ignition locks, the user was able to enter and drive the car. Recently, car manufacturers have introduced Passive Keyless Entry and Start (PKES) systems that allow users to open and start their cars while having their car keys ’in their pockets’. In this work, we analyze the security of PKES systems and show that they are vulnerable to relay attacks. In a relay attack, the attacker places one of her devices in the proxim- ity of the key, and the other device in the proximity of the car. The attacker then relays messages between the key and the car, enabling the car to be opened and started even if the key is physically far from the car.
Related work:
- Aurelien Francillon, Boris Danev, Srdjan Capkun
Relay Attacks on Passive Keyless Entry and Start Systems in Modern Cars
In Proceedings of the Network and Distributed System Security Symposium (NDSS), 2011
Preceding technical report: Cryptology ePrint Archive: Report 2010/332, 2010 [Download PDF (PDF, 1 MB)]
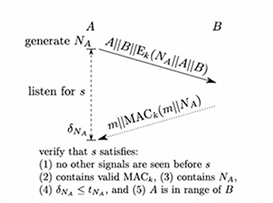
Secure Ranging with Message Temporal Integrity
In this paper, we address the problem of delay attacks on radio frequency time of arrival (ToA) secure ranging. In secure ranging, two mutually trusted devices try to determine their distance in the presence of an attacker. A delay attack consists of delaying the ranging messages exchanged between the devices, resulting in an increase of the measured message arrival times and thus in an increase of the measured distance. In this work, we propose the first secure ranging protocol that enables the detection of delay attacks on ranging. This protocol therefore enables two trusted devices to obtain a secure estimate of their mutual distance; existing solutions enabled the devices only to obtain an upper bound on their mutual distance. We further discuss possible implementations of our secure ranging protocol using Ultra-Wide-Band radio technology. Finally, we introduce and formally define the notion of message temporal integrity, a message security property which relates to message delay and advancement.
Message Temporal Integrity Protocol
Related Work:
Nils Ole Tippenhauer, Kasper Bonne Rasmussen, Srdjan Capkun
Secure Ranging With Message Temporal Integrity
Cryptology ePrint Archive: Report 2009/602, 2009 [Download PDF (PDF, 526 KB)]
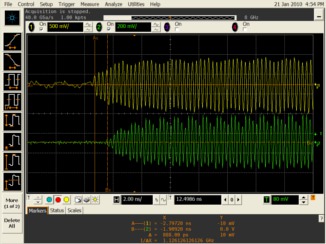
Realization of RF Distance Bounding
One of the main obstacles for the wider deployment of radio (RF) distance bounding is the lack of platforms that implement these protocols. We address this problem and we build a prototype system that demonstrates that radio distance bounding protocols can be implemented to match the strict processing that these protocols require. Our system implements a prover that is able to receive, process and transmit signals in less than 1ns. The security guarantee that a distance bounding protocol built on top of this system therefore provides is that a malicious prover can, at most, pretend to be about 15cm closer to the verifier than it really is. To enable such fast processing at the prover, we use specially implemented concatenation as the prover's processing function and show how it can be integrated into a distance bounding protocol. Finally, we show that functions such as XOR and the comparison function, that were used in a number of previously proposed distance bounding protocols, are not best suited for the implementation of radio distance bounding.
Related work:
- Kasper Bonne Rasmussen, Srdjan Capkun
Realization of RF Distance Bounding
In Proceedings of the USENIX Security Symposium, 2010 [Download PDF (PDF, 946 KB)]
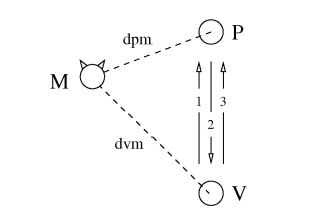
Location Privacy of Distance Bounding Protocols
Distance bounding protocols have been proposed for many security critical applications as a mean of getting an upper bound on the physical distance to a communication partner. As such, distance bounding protocols are executed frequently, e.g., to keep node map’s up to date, etc. We analyze distance bounding protocols in terms of their location privacy and we show that they leak information about the location and distance between communicating partners even to passive attackers. This location and distance information may be highly sensitive since it can form the basis for access control, key establishment, or be used as input to location aware applications. We analyze, in a number of scenarios, how much information distance bounding protocols leak. We further discuss several straightforward countermeasures and show why they do not provide adequate protection against distance leakage. Finally, we propose a location private distance bounding protocol that maintains the properties of existing distance bounding protocols while leaking no information about the distance measured between the communicating parties.
Related work:
- Kasper Bonne Rasmussen, Srdjan Capkun
Location Privacy of Distance Bounding Protocols
In Proceedings of the ACM Conference on Computer and Communications Security (CCS), 2008 [Download PDF (PDF, 309 KB)]
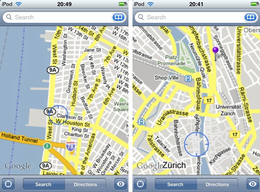
Location Spoofing on Wlan-Based Localization
We analysed conventional public WLAN-based localization systems on the example of the WPS of Skyhook, which is being used in Apple's iPhone and iPod touch devices. By using a combination of access point spoofing and WLAN jamming, we were able to displace the location returned by these devices to an arbitrary position. Legitimate access points existing at the victim's position were jammed using software radios so that the victim was unable to obtain its correct position. Then, the target location was spoofed by imitating access points at that location. As a result, we successfully displaced the devices from the location in Zurich, Switzerland, to New York City.
Position spoofing on the iPod
Related work:
- Nils Ole Tippenhauer, Kasper Bonne Rasmussen, Christina Pöpper, Srdjan Capkun
Attacks on Public WLAN-based Positioning
In Proceedings of the ACM/Usenix International Conference on Mobile
Systems, Applications and Services (MobiSys), 2009 [Download PDF (PDF, 1.7 MB) | Download bibtex (BIB, 5 KB) | Download talk video (FLV, 128 MB)]
Related Technical Report 599, ETH Zürich, System Security Group, April 2008. [Download PDF (PDF, 567 KB) | Download bibtex (BIB, 313 Bytes) | external page online version]

UWB-Based Secure Ranging and Localization
We propose and implement a novel ID-based secure ranging protocol. Our protocol is inspired by existing authenticated ranging and distance-bounding protocols, and is tailored to work on existing Ultra Wide Band (UWB) ranging platforms. Building on the implementation of secure ranging, we further implement a secure localization protocol that enables the computation of a correct device location in the presence of an adversary. We study how various implementations of secure ranging and localization protocols impacts their security and performance. We further propose modifications to these protocols to increase their security and accuracy.
To the best of our knowledge, this is the first implementation of a RF Time-of-Arrival (ToA) secure localization system.
- Nils Ole Tippenhauer, Srdjan Capkun
ID-based Secure Distance Bounding and Localization
In Proceedings of ESORICS (European Symposium on Research in Computer Security), 2009 [Download PDF (PDF, 559 KB) | Download bibtex (BIB, 5 KB)]
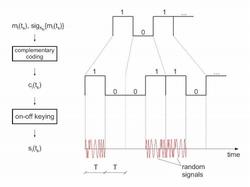
Secure Broadcast Localization and Time Synchronization (based on Integrity-Coding)
We propose SecNav, a new protocol for securing wireless navigation systems. This protocol secures localization and time-synchronization in wireless networks by relying on devices’ awareness of presence in the coverage area of navigation stations. We perform a detailed security analysis of SecNav and we show that, compared to existing secure navigation approaches, it prevents the widest range of attacks on navigation.
Related publications:
- K. B. Rasmussen, S. Capkun, and M. Cagalj
SecNav: Secure Broadcast Localization and Time Synchronization in Wireless Networks (extended abstract), in Proceedings of ACM MobiCom 2007 [Download PDF (PDF, 664 KB)]
(related Technical Report 546, ETH Zürich, IFW, February 7, 2007. [Download PDF (PDF, 1.2 MB)])
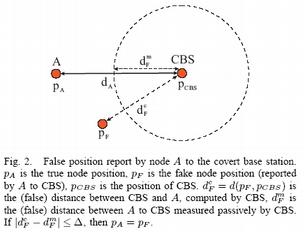
Secure Localization Based on Hidden and Mobile Base Stations
In this work, we propose a new approach to secure localization based on hidden and mobile base stations. Our approach enables secure localization with a broad spectrum of localization techniques: ultrasonic or radio, based on received signal strength or signal time of flight. Through several examples we show how this approach can be used to secure node-centric and infrastructure-centric localization schemes. We further show how this approach can be applied to secure localization in sensor networks.
We rely on a set of covert base stations (CBS), whose positions are not known to the attacker at the time of the execution of secure positioning. In our system, positions of covert base stations represent a secret input (a key) to the system. Covert base stations are typically passive and can be realized by hiding or disguising static base station or by the random motion of mobile base stations. Our solution relies on the premise that the devices cannot lie about their locations if the location of at least one verification station (i.e., infrastructure station) is hidden.
The movie on the left illustrates the basic idea behind secure localization based on mobile base stations. In the animation the moving dot is a mobile base station that sends out challenges to the nodes in the network. When a node receives a challenge it turns yellow. The node then replies to that challenge and when the mobile base station picks up a reply, the node is marked as confirmed (light blue). The assumption is that the node does not know where the mobile base station is when it has to reply and therefore it does not know how to fake its position. In this animation the mobile base station uses random walk with a step size equal to its transmission range.
Related publications and presentations:
- S. Capkun, K. B. Rasmussen, M. Cagalj, and M. Srivastava
Secure Location Verification With Hidden and Mobile Base Stations,
in IEEE Transactions on Mobile Computing, April 2008 [Download PDF (PDF, 1.9 MB), Download simulation (AVI, 1 MB)]
- S. Capkun, M. Cagalj, and M. Srivastava,
Securing Localization With Hidden and Mobile Base Stations,
in Proceedings of IEEE INFOCOM 2006 [Download PDF (PDF, 310 KB)]
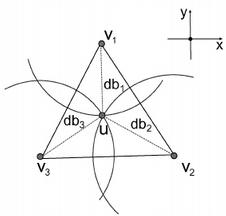
Verifiable Multilateration
Verifiable Multilateration is a mechanism that enables location verification and secure localization of wireless devices in the presence of external and internal attackers. This mechanism relies on authenticated ranging or distance bounding within a verification triangle (triangular pyramid) formed by the location verifiers (i.e., by the localization infrastructure).
RF-based authenticated ranging and distance boudning hold properties that attackers (in the case of authenticated ranging external attackers and in the case of distance bounding internal and external attackers) can only enlarge (but not reduce) the measured distance between the infrastructure and the node. The intuition behind the verifiable multilateration algorithm is the following: because of the distance bounding property, the claimant can only pretend to be more distant from the verifier than it really is. If it increases the measured distance to one of the verifiers in order to keep the position consistent, the claimant needs to prove that at least one of the measured distances to other verifiers is shorter than it actually is, which it cannot because of the distance bounding. This property holds only if the position of the claimant is determined within the triangle formed by the verifiers. This can be explained with a simple example: if an object is located within the triangle and it moves to a different position within the triangle, it will certainly reduce its distance to at least one of the triangle vertices. The same properties hold if an external attacker enlarges distances between verifiers and an honest claimant.
Related publications and presentations:
- S. Capkun and J.-P. Hubaux,
Secure positioning of wireless devices with application to sensor networks,
in Proceedings of IEEE INFOCOM 2005 [Download PDF (PDF, 541 KB)]
- S. Capkun and J.-P. Hubaux,
Secure positioning in wireless networks,
IEEE Journal on Selected Areas in Communications: Special Issue on Security in Wireless Ad Hoc Networks, February 2006 [Download PDF (PDF, 639 KB)]
Secure RSS-Based Localization in Sensor Networks
We propose a secure localization scheme for sensor networks based on the received signal strength (RSS) ranging techniques. Our scheme enables the network authority to obtain locations of sensor nodes in the presence of an attacker. The proposed scheme uses a small number of anchor nodes with known locations that provide points of reference from which the sensors’ locations are computed. This scheme makes use of robust localization and time synchronization primitives which, appropriately combined, enable the detection of attacks on localization, within a realistic attacker model. We perform an in-depth security analysis of our scheme and we demonstrate its feasibility on Mica2 sensor platform.
Related publication:
- S. Capkun, S. Ganeriwal, F. Anjum and M. Srivastava,
Secure RSS-based Localization in Sensor Networks,
Technical Report 529, ETH Zürich, 09 2006 [Download PDF (PDF, 151 KB)]
Secure Proximity Verification in Mobile ad hoc Networks
In this work we present SECTOR, a set of mechanisms for the secure verification of the time of encounters between nodes in multi-hop wireless networks. This information can be used notably to prevent wormhole attacks (without requiring any clock synchronization), to secure routing protocols based on last encounters (with only loose clock synchronization), and to control the topology of the network. SECTOR is based primarily on distance-bounding techniques, on one-way hash chains and on Merkle hash trees.
Related publication:
- S. Capkun, L. Buttyán, and J.-P. Hubaux,
SECTOR: Secure Tracking of Node Encounters in Multi-hop Wireless Networks,
In Proceedings of the 1st ACM Workshop on Security of Ad Hoc and Sensor Networks (SASN), October 2003. [Download PDF (PDF, 164 KB)]
OTHER CONTRIBUTIONS
Distance Enlargement and Reduction Attacks on Ultrasonic Ranging
This work demonstrates two attacks on ultrasonic ranging systems: the wormhole attack, by which the attackers reduce the distance measured between two honest nodes, and the pulse-delay attack, by which the attackers enlarge the measured distance. With these attacks, we show that the attackers can arbitrarily modify distances measured with ultrasonic ranging, despite the authentication and integrity protection of the messages used in the ranging protocol.Related presentation:
- S. Sedighpour, S. Capkun, S. Ganeriwal, and M. Srivastava,
Implementation of Attacks on Ultrasonic Ranging Systems, demo,
SENSYS 2005. Demo description [Download PDF (PDF, 61 KB)], Poster [Download PDF (PDF, 89 KB)]
ROPE: Robust Position Estimation in Sensor Networks
This work addresses secure localization and location verification in wireless sensor
networks (WSN). We propose a robust positioning system called ROPE that allows sensors to determine their location without centralized computation. In addition, ROPE provides a location verification mechanism that verifies the location claims of the sensors before data collection.
Related publication:
- L. Lazos, S. Capkun, and R. Poovendran,
ROPE: Robust Position Estimation in Wireless Sensor Networks,
in Proceedings of IPSN 2005 [Download PDF (PDF, 954 KB)]